如题,目的是实现以下目标 1、VLESS + Reality节点正常使用,使用自己域名证书,运行在443端口 2、6000端口运行Alist(随便一个伪装网站),通过xray回落实现浏览器通过http访问看到的是可以正常使用的alist(伪装网站),节点通过vless访问可以正常进入xray代理 3、8443端口运行AdGuardHome,通过Nginx反代到443随机路径上,正常提供DOH服务
PS:以上全部,只使用1个域名,1个端口实现,使用x-ui自动更新的证书
有什么实际意义 1、更好的伪装,Http回落 2、自建DNS服务器,可以看到DNS查询日志并DNS去广告
如果你觉得有用,下面是详细配置
AdGuardHome面板地址:https://domain.com/adguard/ Doh地址:https://domain.com/dns-q/KypfxMjq7dZ6wJKDqU5CMFqHLxehwcNG
Xray
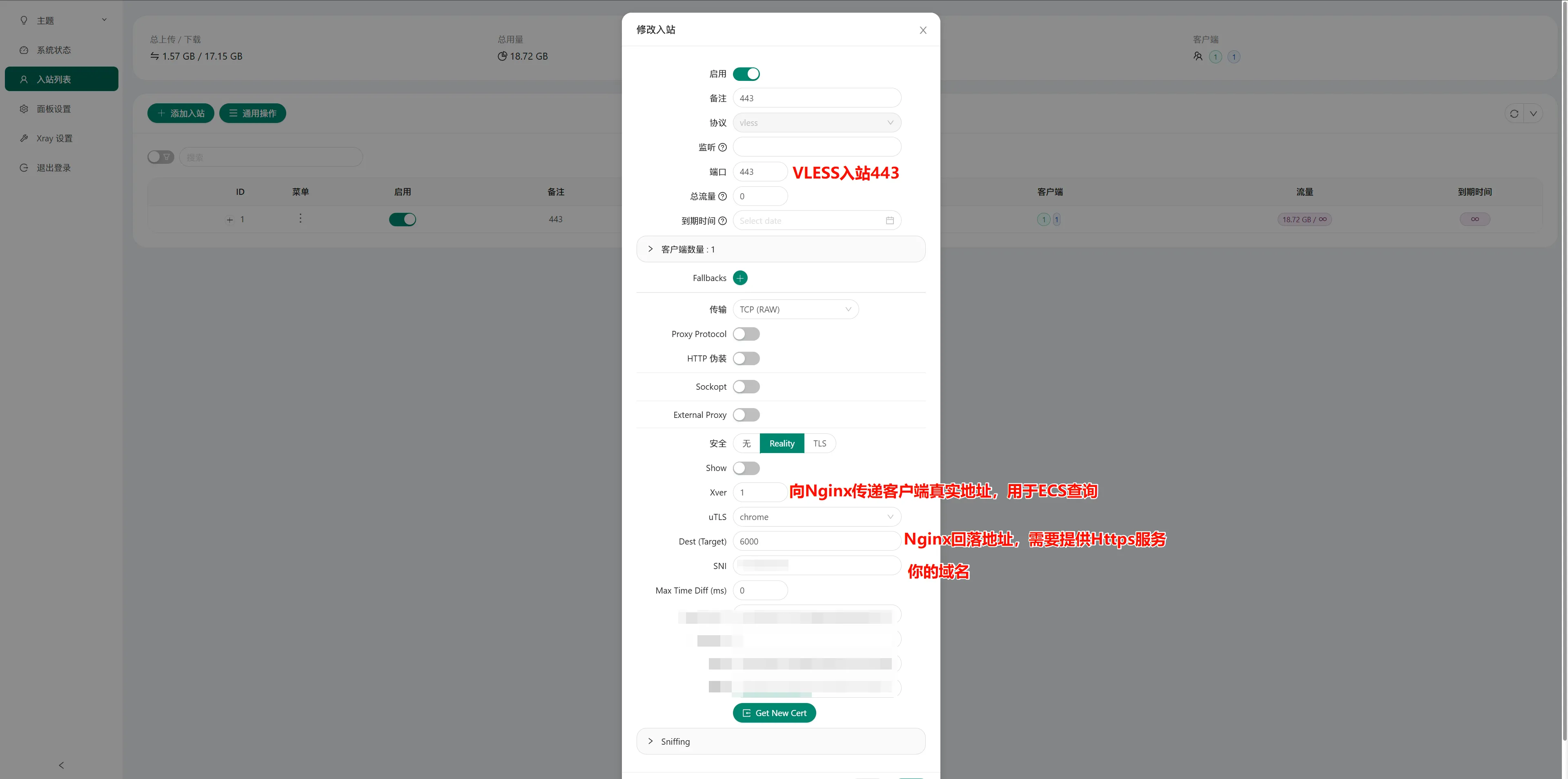
Nginx
所使用域名由domain.com代替
worker_processes auto;
error_log /var/log/nginx/error.log;
pid /run/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
log_format main '$proxy_protocol_addr - $remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
keepalive_timeout 65;
server {
listen 80;
return 301 https://$host$request_uri;
}
server {
listen 127.0.0.1:6000 ssl http2 proxy_protocol;
server_name domain.com;
set_real_ip_from 127.0.0.1;
real_ip_header proxy_protocol;
ssl_certificate /root/cert/domain.com/fullchain.pem;
ssl_certificate_key /root/cert/domain.com/privkey.pem;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:10m;
ssl_session_tickets off;
location / {
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
proxy_pass http://localhost:5244;
proxy_set_header Host $host;
# proxy_set_header X-Real-IP $remote_addr;
# proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Real-IP $proxy_protocol_addr;
proxy_set_header X-Forwarded-For $proxy_protocol_addr;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /adguard/ {
proxy_pass https://127.0.0.1:8443/;
proxy_redirect / /adguard/;
proxy_cookie_path / /adguard/;
proxy_set_header Host $host;
proxy_ssl_server_name on;
proxy_set_header X-Real-IP $proxy_protocol_addr;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
client_max_body_size 1m;
client_body_buffer_size 256k;
client_body_timeout 60s;
send_timeout 60s;
proxy_connect_timeout 60s;
proxy_read_timeout 60s;
proxy_send_timeout 60s;
proxy_buffer_size 32k;
proxy_buffers 4 16k;
proxy_busy_buffers_size 32k;
proxy_temp_file_write_size 32k;
proxy_ignore_client_abort on;
}
location /dns-q/KypfxMjq7dZ6wJKDqU5CMFqHLxehwcNG {
proxy_pass https://127.0.0.1:8443/dns-query;
proxy_redirect off;
# 设置客户端真实 IP
proxy_set_header X-Real-IP $proxy_protocol_addr;
proxy_set_header X-Forwarded-For $proxy_protocol_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_bind 127.0.0.1;
# 其他必要头部
proxy_set_header Host $host;
proxy_set_header User-Agent $http_user_agent;
proxy_set_header Accept $http_accept;
proxy_set_header Accept-Encoding $http_accept_encoding;
# SSL 配置
proxy_ssl_server_name on;
proxy_ssl_name domain.com;
# DoH 特定配置
proxy_set_header Content-Type $content_type;
proxy_pass_request_headers on;
}
}
}AdGuardHome配置
这里加密的密码是zMHqo82J5PStbqrnTmRtho3Atzo7RBtf 建议先配置好,能正常使用之后再覆盖配置文件,保留你的用户名密码
http:
pprof:
port: 6060
enabled: false
address: 0.0.0.0:3000
session_ttl: 720h
users:
- name: LnfUyrdEFQFkH4kno6DkHngkVYXo7Lc6
password: $2a$10$iLWlfyOHz33vHQtwPoDk8.exlq16UYA/LBQK8AmsztqOFAWATBxue
auth_attempts: 5
block_auth_min: 15
http_proxy: ""
language: ""
theme: auto
dns:
bind_hosts:
- 0.0.0.0
port: 5353
anonymize_client_ip: false
ratelimit: 0
ratelimit_subnet_len_ipv4: 24
ratelimit_subnet_len_ipv6: 56
ratelimit_whitelist: []
refuse_any: true
upstream_dns:
- https://8.8.8.8/dns-query
- https://1.1.1.1/dns-query
upstream_dns_file: ""
bootstrap_dns:
- 9.9.9.10
- 149.112.112.10
- 2620:fe::10
- 2620:fe::fe:10
fallback_dns:
- 9.9.9.10
- 149.112.112.10
upstream_mode: load_balance
fastest_timeout: 1s
allowed_clients: []
disallowed_clients: []
blocked_hosts:
- version.bind
- id.server
- hostname.bind
trusted_proxies:
- 0.0.0.0/0
cache_size: 4194304
cache_ttl_min: 0
cache_ttl_max: 0
cache_optimistic: false
bogus_nxdomain: []
aaaa_disabled: true
enable_dnssec: false
edns_client_subnet:
custom_ip: ""
enabled: true
use_custom: false
max_goroutines: 300
handle_ddr: true
ipset: []
ipset_file: ""
bootstrap_prefer_ipv6: false
upstream_timeout: 10s
private_networks: []
use_private_ptr_resolvers: false
local_ptr_upstreams: []
use_dns64: false
dns64_prefixes: []
serve_http3: false
use_http3_upstreams: false
serve_plain_dns: true
hostsfile_enabled: true
pending_requests:
enabled: true
tls:
enabled: true
server_name: hk.violab.net
force_https: false
port_https: 8443
port_dns_over_tls: 853
port_dns_over_quic: 853
port_dnscrypt: 0
dnscrypt_config_file: ""
allow_unencrypted_doh: false
certificate_chain: ""
private_key: ""
certificate_path: /root/cert/hk.violab.net/fullchain.pem
private_key_path: /root/cert/hk.violab.net/privkey.pem
strict_sni_check: false
querylog:
dir_path: ""
ignored: []
interval: 2160h
size_memory: 1000
enabled: true
file_enabled: true
statistics:
dir_path: ""
ignored: []
interval: 2160h
enabled: true
filters:
- enabled: true
url: https://adguardteam.github.io/HostlistsRegistry/assets/filter_1.txt
name: AdGuard DNS filter
id: 1
- enabled: false
url: https://adguardteam.github.io/HostlistsRegistry/assets/filter_2.txt
name: AdAway Default Blocklist
id: 2
whitelist_filters: []
user_rules: []
dhcp:
enabled: false
interface_name: ""
local_domain_name: lan
dhcpv4:
gateway_ip: ""
subnet_mask: ""
range_start: ""
range_end: ""
lease_duration: 86400
icmp_timeout_msec: 1000
options: []
dhcpv6:
range_start: ""
lease_duration: 86400
ra_slaac_only: false
ra_allow_slaac: false
filtering:
blocking_ipv4: ""
blocking_ipv6: ""
blocked_services:
schedule:
time_zone: Local
ids: []
protection_disabled_until: null
safe_search:
enabled: false
bing: true
duckduckgo: true
ecosia: true
google: true
pixabay: true
yandex: true
youtube: true
blocking_mode: default
parental_block_host: family-block.dns.adguard.com
safebrowsing_block_host: standard-block.dns.adguard.com
rewrites: []
safe_fs_patterns:
- /opt/AdGuardHome/userfilters/*
safebrowsing_cache_size: 1048576
safesearch_cache_size: 1048576
parental_cache_size: 1048576
cache_time: 30
filters_update_interval: 24
blocked_response_ttl: 10
filtering_enabled: true
parental_enabled: false
safebrowsing_enabled: false
protection_enabled: true
clients:
runtime_sources:
whois: true
arp: true
rdns: false
dhcp: true
hosts: true
persistent: []
log:
enabled: true
file: /opt/AdGuardHome/adg.log
max_backups: 0
max_size: 100
max_age: 3
compress: false
local_time: false
verbose: false
os:
group: ""
user: ""
rlimit_nofile: 0
schema_version: 29
禁用公开端口
设置端口:853(Dot),8443(Doh),3000(AdGuardHome面板)只允许本地访问
iptables -A INPUT -p tcp --dport 853 -s 127.0.0.1 -j ACCEPT
iptables -A INPUT -p udp --dport 853 -s 127.0.0.1 -j ACCEPT
iptables -A INPUT -p tcp --dport 8443 -s 127.0.0.1 -j ACCEPT
iptables -A INPUT -p tcp --dport 3000 -s 127.0.0.1 -j ACCEPT
iptables -A INPUT -p tcp --dport 5353 -s 127.0.0.1 -j ACCEPT
iptables -A INPUT -p tcp --dport 853 -j DROP
iptables -A INPUT -p udp --dport 853 -j DROP
iptables -A INPUT -p tcp --dport 8443 -j DROP
iptables -A INPUT -p tcp --dport 3000 -j DROP
iptables -A INPUT -p tcp --dport 5353 -j DROP